
Port Scanning – Exposing Your Network’s Points Of Entry
In computer networking, ports are points of entry to your computer – virtual origins and/or destinations of network connections. Port number definition and standardisation is overseen by the Internet Assigned Numbers Authority (IANA). Based on the list maintained by IANA, there are three types of ports amongst the total number of 65536:
1. Well-known ports (also known as system ports). The port numbers range from 0 to 1023. These are reserved for services commonly used across the Internet. Some well-known port numbers are as follows: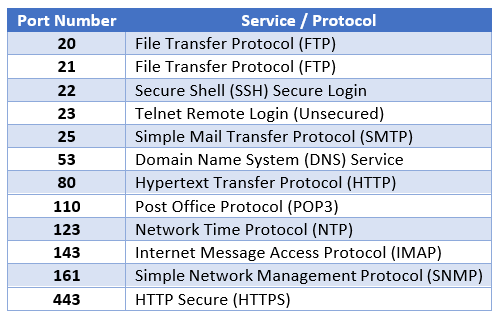
2. Registered ports. The port numbers range from 1024 to 49151. Service vendors who wish to register a certain port for their own server applications. They are uncommonly used as compared to the well-known ports.
3. Dynamic ports (also known as private ports). The port numbers range from 49152 to 65535. They are available for use by any application.
As you can see, there is a wealth of information available to anyone who is able to access it – by scanning the ports of a computer. Attackers who perform port scanning will be able to determine (among other things) services that are currently running on the computer. They can then formulate a path of attack based on the information gathered.
Port Scanning Techniques
There are a variety of ways port scanning is performed. But they fall into three general categories:
1. Ping Scan – The simplest form of port scanning, it utilises the Internet Control Message Protocol (ICMP) echo request.
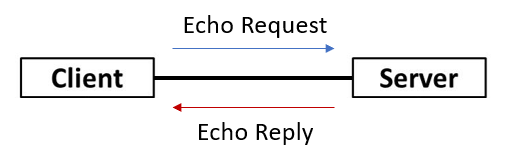
Figure 1: ICMP echo request and reply
2. Transmission Control Protocol (TCP) Scan – This scan utilises the three-way handshake feature of the connection-oriented TCP to perform its scans. Once again, there are a large variety of ways to use TCP in the scanning process.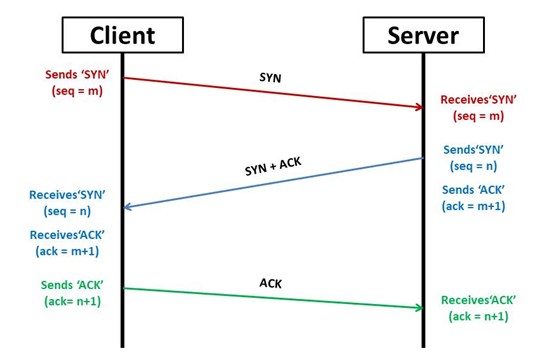
Figure 2: TCP 3-way handshake
3. User Datagram Protocol (UDP) Scan – This scan utilises the connectionless UDP as its vehicle. This is usually used when a specific payload to a specific service is sent.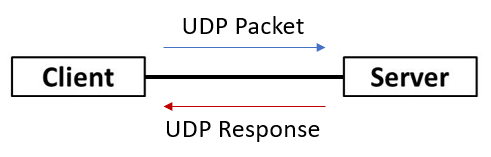
Figure 3: UDP packet and response
Different techniques are used based on the requirements and/or objectives of the scan. Typically, an attacker would use a technique that provides some level of stealth, so that his/her reconnaissance attempts would not be detected and blocked.
A Powerful Network Scanner: Nmap
There is a myriad of tools available to perform the different port scanning techniques. The most popular network scanner would be Nmap.
Figure 4: Nmap GUI, Zenmap, taken from https://nmap.org/zenmap
Usually used in the terminal, Nmap also has an official GUI, named Zenmap (Figure 4). There are simply too many functionalities to Nmap to list in this article (e.g. banner grabbing, service enumeration, OS fingerprinting, etc); you may refer to the Nmap documentation here.
Port scanning can be done very easily with a tool as readily available as Nmap. That just emphasises the importance of placing countermeasures to prevent information leakage via port scanning.
Protecting Your Web Application
Instead of leaving your web servers open to any scans and revealing sensitive information, as a web server owner or administrator, you can take steps to defend your web servers from being enumerated from port scanning.
1. Install a Firewall – A firewall can help prevent unauthorised access to your network. It ensures that unused ports are closed or made invisible, so that it cannot be used for any attack. An advanced firewall can also detect if a port scan is in progress and halt the scan appropriately.
2. Regular Internal Port Scanning – The best way to know if you have any gaps is to perform port scanning internally, so that you can know first hand which ports are exposed to the public. Thereafter with that information in mind, you can take the appropriate steps to close and remove visibility of the port.
WebOrion Protector
The WebOrion Protector is an industry-leading web application firewall and DDoS mitigation solution, which can stop attackers from causing harm to your web application. It can provide complete web application security for all platforms. For more information on WebOrion Protector, you may visit this page. If you are interested, do drop us an email at sales@cloudsine.tech.

